How Crypto Projects Can Prevent Hacks in 2025

In 2025, there was a notable increase in scams, hacks and cryptographic exploits. More than 2 billion dollars were stolen in cryptocurrency services in the first six months. Mitchell Amador, CEO of Imunefi, a web security platform3, estimates that many teams now consider security as a “pre-launch check box”.
In an exclusive interview with Beincrypto, Amador also underlined how the payment of millions of pirates to identify the bugs can prevent billions of losses and can be more effective than traditional cybersecurity.
Why does the crypto hacks increase in 2025?
In a recent report, Beincrypto stressed that 2025 is promising to become the worst year ever recorded in terms of stolen total value. This year, the industry has already attended its greatest violation to date, the Hack of Bybet.
In addition, hackers continue to steal millions of dollars in crypto exchanges and related companies.
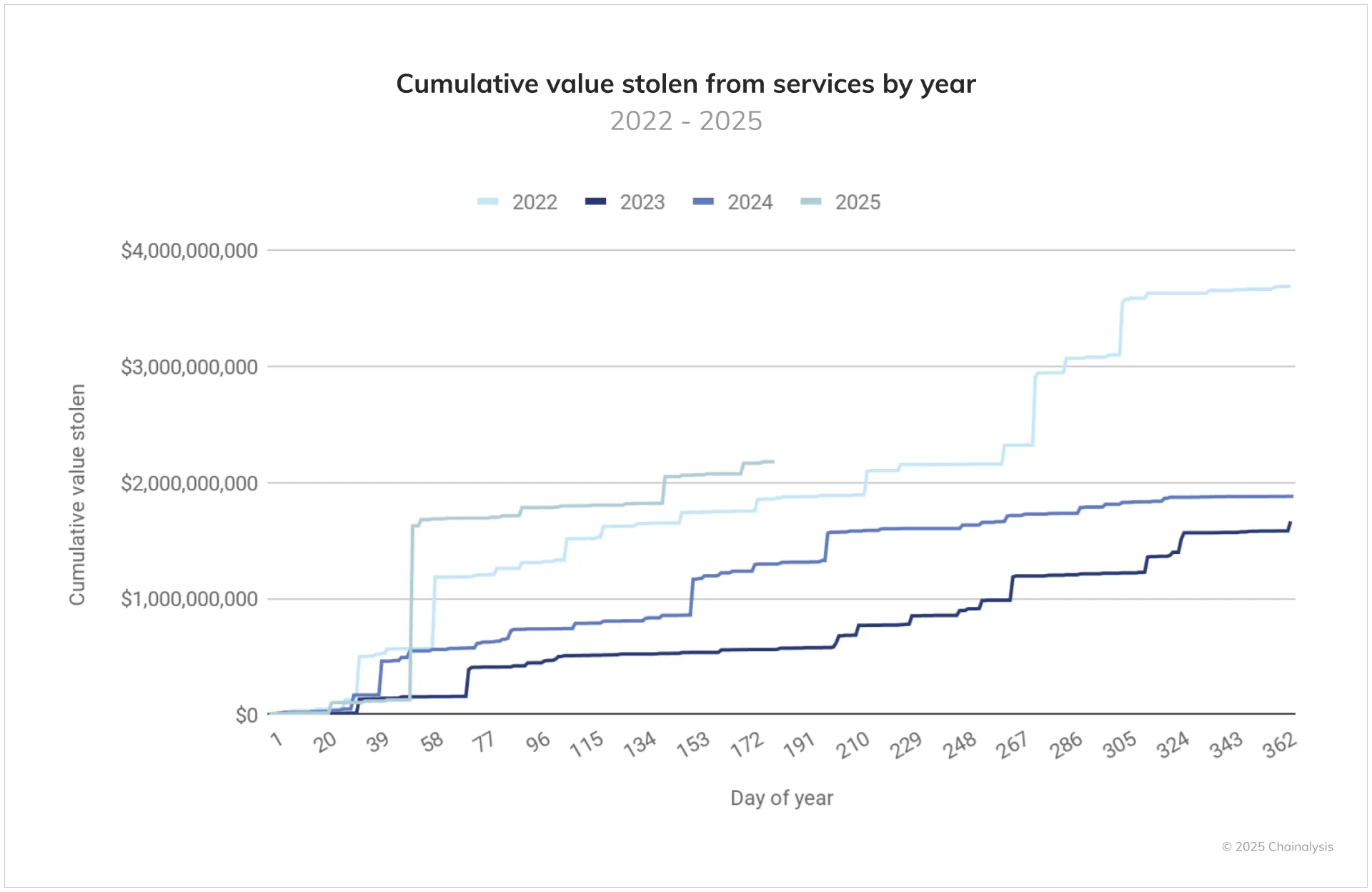
In fact, the analysis chain predicted that the total amount of stolen funds from cryptography services could exceed $ 4.3 billion by the end of the year. This portrays a dark perspective for industry, with continuous risks threatening its security and stability.
Above all, TRM Labs revealed that in the first half of 2025, more than 80% of stolen funds result from infrastructure violations. But why is it going?
According to Amador, the climbing of crypto hacks this year stems from a fundamental defect in the number of projects are approaching security.
“2025 is the year of the crypto crypto mentality.
He explained that after the launch, many projects improve intelligent contracts, integrate oracles or change governance structures without reviewing their original risk models. This lack of continuous risk assessment has led to an increase in post-receipt exploits.
“Safety must go from static to continuous.
How bug bonuses are the key to preventing cryptographic hacks
While security measures must be constantly evolving, the CEO of Immunofi has also pleaded for bug bonuses. According to him, they are more effective than traditional cybersecurity methods in cryptographic space.
For the context, a bug bonus is a reward offered by organizations to people who identify and signal security vulnerabilities in their software or systems. These “ethical pirates” or Bogue bonus hunters help companies identify and resolve weaknesses before malicious actors can exploit them.
The awards are generally monetary and vary depending on the gravity, the complexity and the potential impact of the reported bug.
Amador noted that the key to preventing exploitation is to make defense against attacks more profitable than launching them. This is where well -designed bonus bonuse programs come into play.
“The crypto returns the rules. In web2, attackers need motivation. In the crypto, money is motivation. If you launch an intelligent contract with $ 100 million, you simply put a price on each bug.
It should be noted that white hat hackers and black hats hacks can have similar technical skills, but their motivations differ considerably. Black Hat Hackers uses vulnerabilities for personal gain or malicious intention, causing damage to individuals or organizations.
On the other hand, white hat hackers work legally and ethically to improve cybersecurity. So, what makes some hackers choose the Chemin du Chapeau Blanc?
“Three things: confidence, increase and recognition. If the hackers know that a platform will pay enough and quickly, they return. If the process is troubled or if the payments are weak, they become Blackhat,” said Amador to be incrypto.
In addition, the executive stressed that the best white hats today are not only individuals but are part of a world force. Elite security researchers leave traditional companies to form a decentralized and deputy security swarm, responding to threats between real -time ecosystems. This approach represents the future of defense – collaborative, rapid and focused on reputation.
Although it may seem simple in theory, in practice, the management of ethical hacking efforts is quite complex. As Amador explained,
“The coordination of real -time responses to live threats in web3 is like defusing a public bomb. If the teams move too slowly, they lose funds. If they move too quickly or without clear authority, they risk the counterpoup. ”
Amador told intense negotiations where immunity was mediated between protocols and whitehats compared to critical vulnerabilities. In cases where bonuses were not pre -established or disagreements appeared on the severity of a bug, the role of immunofi as a neutral mediator provided fair resolutions.
“The most intense cases often occur outside the spotlights, but they highlight the need for clear disclosure process and pre-engaged incentives. It is a question of managing the confidence under pressure,” said the CEO to Beincryptto.
The future of web security3
Despite the importance of Bug bonuses, Amador stressed that they are only one layer of safety. He said the next web security phase will be automated, continues and centered on humans.
“We need autonomous systems that digitize the code, model behavioral threats and instantly react, exploits of phishing and risk of initiate. We also build Safe Harbor, an initiative that allows the Whitehats elite to operate as a 24/7 threat team.
However, Amador stressed that crypto will remain vulnerable until these systems are the norm. Once these security measures are in place, they will unlock a new era of institutional investment and public confidence, paving the way for a safer future.
Non-liability clause
Following the directives of the Trust project, this operating article presents opinions and prospects of experts or individuals in the industry. Beincrypto is dedicated to transparent relationships, but the opinions expressed in this article do not necessarily reflect those of Beincrypto or its staff. Readers must check the information independently and consult a professional before making decisions according to this content. Please note that our terms and conditions, our privacy policy and our non-responsibility clauses have been updated.




