Crypto Criminals are Exploiting Ethereum Pectra’s EIP-7702

The recently introduced intelligent portfolio function of Ethereum, EIP-7702, is examined after Blockchain safety researchers discovered improper use of cybercriminals. After the Pectra upgrade, several portfolio suppliers began to integrate the EIP-7702 features.
Wintermute analysts, a crypto negotiation company, noted that the attackers used 97% of the EIP-7702 portfolio delegations to deploy contracts designed to drain the funds of without distrust.
Pirates use ETHEREUM EIP-7702 to automate mass wallet drainage
EIP-7702 Temporarily allows accounts belonging to the outside (EOAS) to operate as intelligent contract portfolios. The upgrade allows features such as the transaction batch, the expenditure limits, the integration of the passing key and the recovery of the wallet, all without changing the portfolio addresses.
Although these upgrades aim to improve conviviality, malicious actors take advantage of the standard to accelerate fund extractions.
Instead of moving the ETH manually of each compromised portfolio, the attackers now authorize contracts that automatically transmit ETH received to their own addresses.
“Without a doubt, the attackers are one of the first adopters of new capacities. 7702 has never been supposed to be a miracle solution and he has large cases of use,” said Ramulla, product manager at Safe.
Wintermute’s analysis shows that most of these portfolio delegations indicate identical code bases designed to “sweep” ETH from compromise wallets.
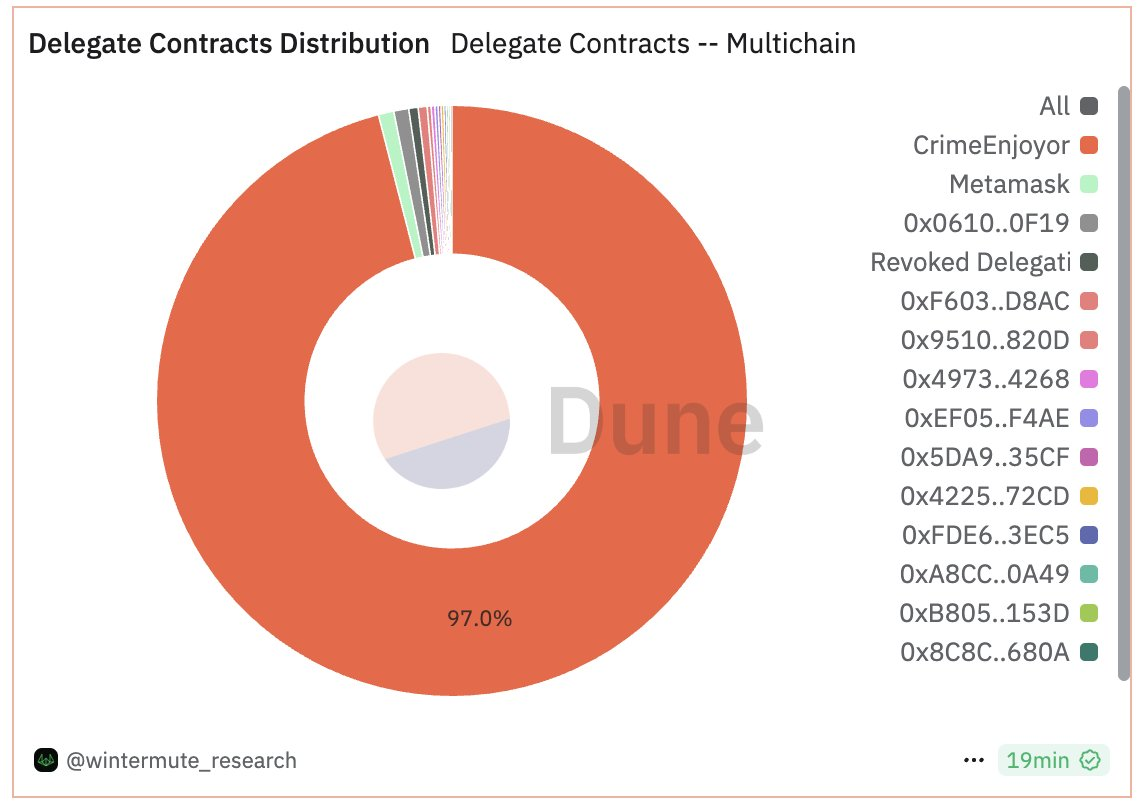
These sweepers automatically transfer the incoming funds to addresses controlled by the attacker. Of nearly 190,000 delegated contracts examined, more than 105,000 were linked to illegal activity.
Koffi, a senior data analyst at Base Network, explained that more than a million portfolios interacted with suspicious contracts last weekend.
He said the attackers did not use EIP-7702 to hack portfolios but to rationalize the flight from wallets with private keys already exposed
The analyst has argued that an out -of -competition implementation includes a reception function that triggers ETH transfers the moment when the funds land in the portfolio, eliminating the need for manual withdrawal.
Yu Xian, founder of the security company Blockchain Slowmist, confirmed that the authors are organized flight groups, and not typical phishing operators. He noted that the automation capacities of the EIP-7702 make it particularly attractive for large-scale exploits.
“The new EIP-7702 mechanism is the most used by parts flight groups (not phishing groups) to automatically transfer wallet addresses with disclosed / mnemonic private keys,” he said.
Despite the magnitude of the operation, there are no confirmed benefits so far.
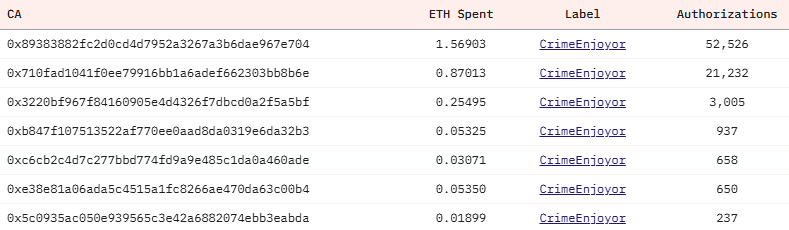
A Wintermute researcher noted that the attackers spent around 2.88 ETH by authorizing more than 79,000 addresses. Only one address has executed nearly 52,000 authorizations, but the target address has received no funds.
Non-liability clause
In membership of the Trust project guidelines, Beincrypto has embarked on transparent impartial reports. This press article aims to provide precise and timely information. However, readers are invited to check the facts independently and consult a professional before making decisions according to this content. Please note that our terms and conditions, our privacy policy and our non-responsibility clauses have been updated.




