Trezor Phishing Attack Breached Support Desk Emails

Earlier in the day, Trezor warned users of a phishing scam from his own help line. An HTML feat allowed criminals to modify Trezor’s assistance emails to include bogus warnings and links to compromised vaults.
We do not currently know if someone fell for this scam, but it may be a small silver lining. This attack could have been carried out using data from previous violations, which makes its culprits difficult to trace.
Crooks target material portfolios
Trezor, a leading material portfolio brand, has been targeted in several hacks, exploits and violations in recent years. The cryptography industry is faced with a wave of attacks at the moment, and it seems that the wallet is again threatened.
Earlier in the day, Trezor warned his clients of a possible phishing scam in the form of assistance emails:
The phishing attack against Trezor customers was rather elegant. The company’s own communications did not give much information on details, only claiming that “there was no violation by e-mail” and that the situation was under control.
However, cyber intelligence surveillance dogs identified a potential threat yesterday, and Trezor treated this as the culprit.
The pirates announced a Trezor security violation on the Dark web, transmitting technical details to the one who pays $ 10,000. This violation involved using an HTML channel to modify the emails sent from the support of Trezor.
Breeding persons could request “help” this email, filling the contact details of a potential victim instead of theirs.
The request would then contain the HTML code, modifying the automatic responses of Trezor to include a phishing attempt. The modified email would go to users, apparently from a legitimate source.
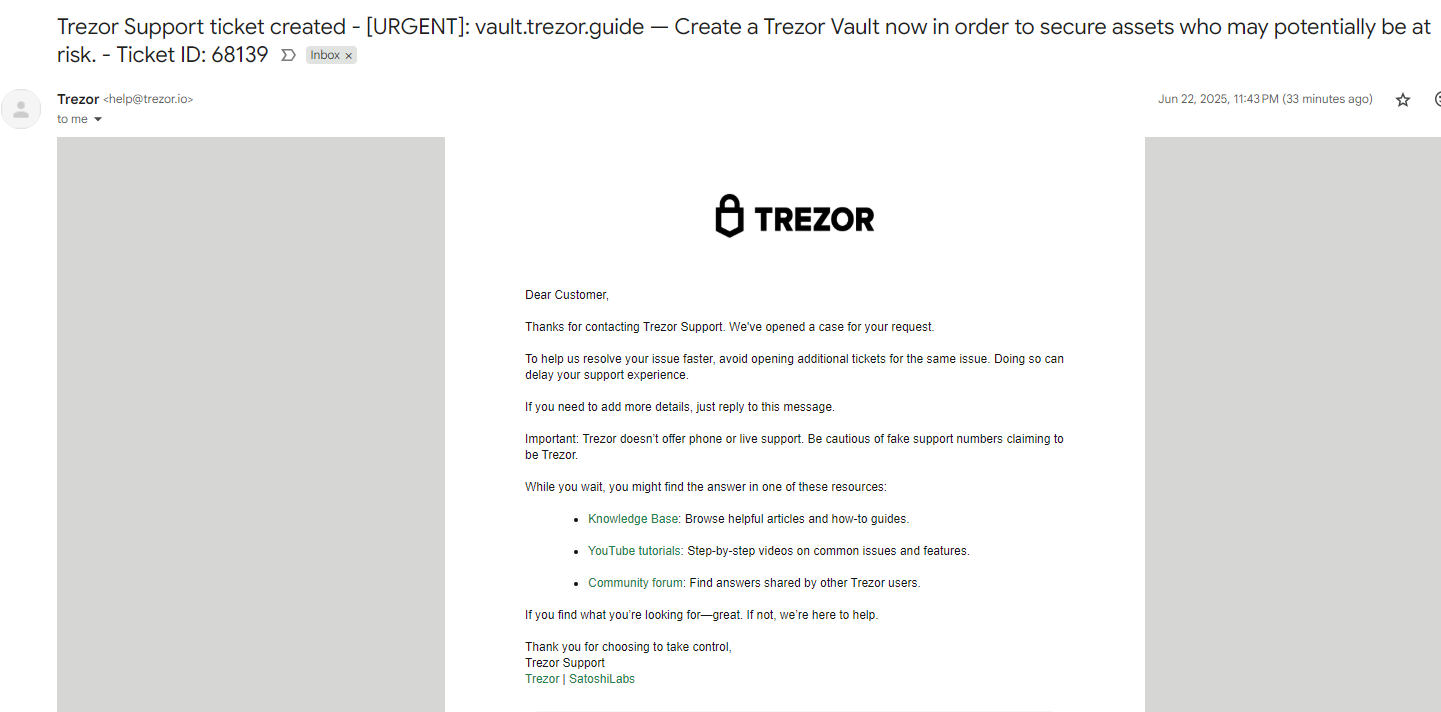
From the user’s point of view, Trezor’s own office would send an email unexpectedly. The body of Trezor’s email would discuss a false “request for support”, while the subject would contain a phishing attempt.
This resolutely web2 scam effort could attract customers from the hardware portfolio to lose everything.
Last year, Trezor warned his customers that 66,000 users who contacted his assistance line may have been compromised. In other words, the contact details of these people may be available on purchase on Seeder websites.
A pirate should buy TREZOR user data and the HTML code to use assistance emails, which could allow large-scale phishing.
In other words, there are no apparent tracks on this phishing author because they did not violate Trezor themselves. Other pirates stole the user data and found the HTML violation, which were both to sell.
Hopefully the investigators will be able to trace these bogus support requests, but it is not clear if it will work.
In recent months, social engineering scams with low skills have managed to penetrate the security of cryptography. Trezor’s material portfolios are very secure, but a phishing attack could attract users to bypass protections.
In this environment, everyone must remain vigilant to prevent fraud.
Non-liability clause
In membership of the Trust project guidelines, Beincrypto has embarked on transparent impartial reports. This press article aims to provide precise and timely information. However, readers are invited to check the facts independently and consult a professional before making decisions according to this content. Please note that our terms and conditions, our privacy policy and our non-responsibility clauses have been updated.




