Was Iran’s Nobitex Laundering Crypto Before the $90 Million Hack?

The hacking of $ 90 million in the greatest exchange of cryptography in Iran, Nobitex, made the headlines of the world newspapers. But the newly surfaced blockchain data show that the breach has exposed something bigger.
A medico-legal report of the Intelligence Company of the Global Ledger Blockchain found that months before the attack on June 18, Nobitex systematically moved user funds using techniques generally associated with money laundering.
Have Iran’s user money laundering funds were before hacking?
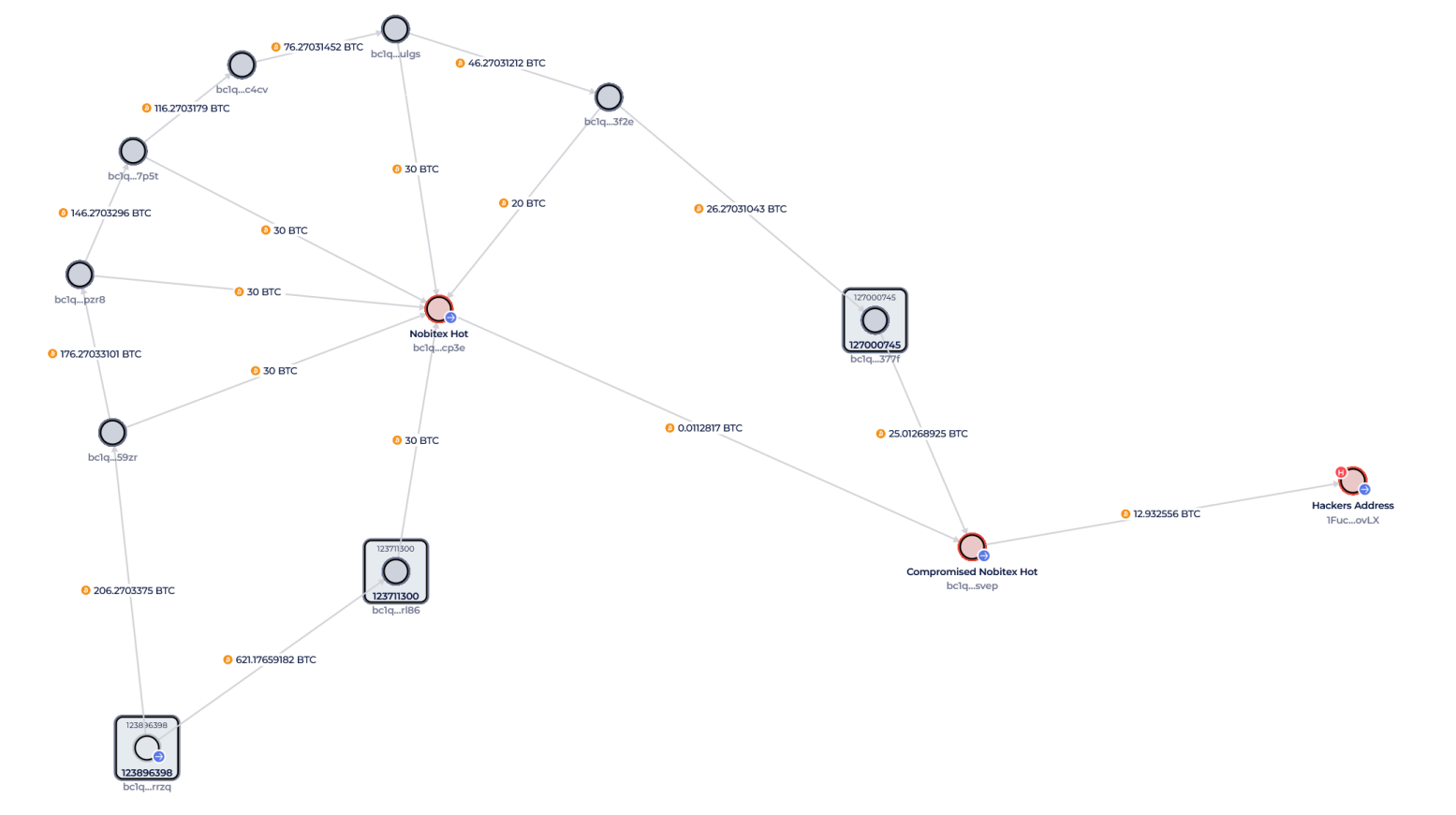
Channel data show that Nobitex has used a method called Peelchaining. It is at this time that large amounts of Bitcoin are divided into smaller and transported pieces through short lifespan wallets.
The technique makes the bottoms of funds difficult and is often used to obscure the origins of money. In the case of Nobitex, analysts found a btc bicycle scheme in coherent songs of 30 years.
Global Ledger also found that Nobitex used temporary deposit and withdrawal addresses – behavior called flea transactions. These single -use addresses surround BTC in new portfolios, disguising the liquidity trails.
The “rescue portfolio” was not new
After hacking, Nobitex said that he had moved the remaining funds as a safety measure. The chain activity has shown a scan of 1,801 BTC (worth ~ 187.5 million dollars) in a newly created portfolio.
But this portfolio was not new. Blockchain data traces its Historic use return until October 2024. The portfolio had long collected chipped funds.
This “rescue portfolio” received several transfers of 20–30 BTC which followed the same whitening reasons, even before the hacking occurred.
Post-hack activity shows continuous control
A few hours after the breach, Nobitex moved the funds of its hot portfolio exposed to another internal address. This complete scan indicated that Nobitex has retained operational control.
On June 19, investigators observed 1,783 BTC transferred again to a new destination portfolio. This corresponded to Nobitex’s public demand to guarantee its assets, but now with an additional context.
The flows suggest that rather than reacting to piracy, Nobitex simply followed his pre -existing money laundering game book.
The pro-Israeli hacking group Gonjeshke Darande published files exposing the structure of the internal portfolio of Nobitex.
The hack may have shocked users, but blockchain data show that Nobitex had already moved funds in this way for months.
The old portfolios linked to the exchange regularly sent bitcoin to new wallets. From there, the funds were divided into smaller quantities and moved again and again – often in 20 or 30 BTC.
This method makes it more difficult for monitoring all money. This is similar to the way some people hide their traces when moving funds via crypto.
What is important is that it was not something that Nobitex started after hacking. They had done it long before, and they continued to do it after –almost as if it was a standard procedure.
A particular portfolio –BC1Q… RRZQ– See again and again. He has received many user deposits and seems to be the starting point for many of these funds of funds that are difficult to trace.
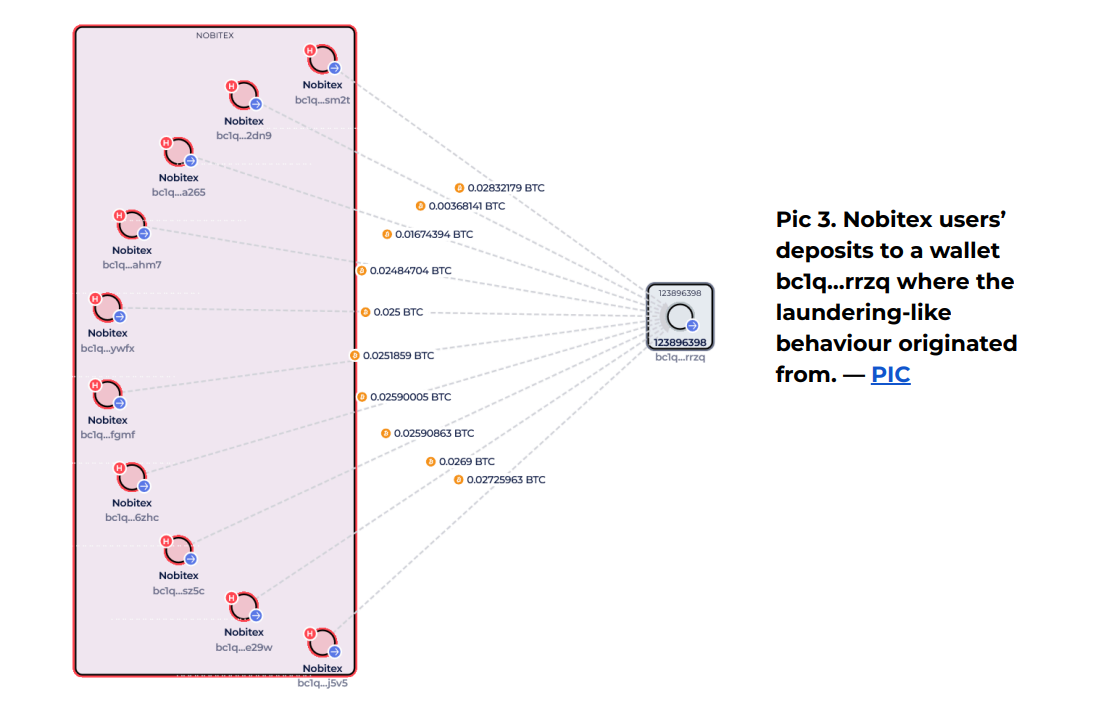
In short, hacking did not change Nobitex how it managed the funds. It just brought current activity behind the scenes in the eyes of the public.
Non-liability clause
In membership of the Trust project guidelines, Beincrypto has embarked on transparent impartial reports. This press article aims to provide precise and timely information. However, readers are invited to check the facts independently and consult a professional before making decisions according to this content. Please note that our terms and conditions, our privacy policy and our non-responsibility clauses have been updated.




